IoT. Internet of Things. Not something that holds a lot of interest for me. If package thieves were a concern, then I could see getting a webcam for the front porch. But as I recently learned, Google has rolled streaming media into its Home concept.
This is the Cast tab in the Google Chrome browser on my desktop PC when I am not using Chromecast.
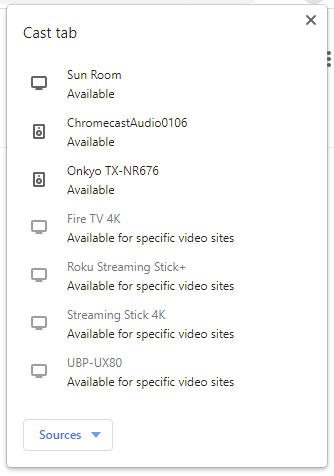
This is the Cast tab when I am casting. Not from the PC, but from my Pixel 4a phone, going to Chromecast Audio on the upstairs stereo.
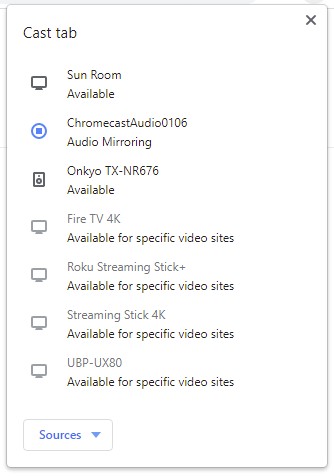
So of course this is how it looks when casting from the phone to the Onkyo A/V receiver downstairs.
When Google Chrome is running it finds compatible devices on the local network and maintains connections to poll for changes.
TCP 192.168.1.179:63387 Chromecast:8008 ESTABLISHED
TCP 192.168.1.179:63388 StreamingStick4K:8060 CLOSE_WAIT
TCP 192.168.1.179:63390 RokuStreamingStick:8060 CLOSE_WAIT
It makes sense to check casting devices, but it raises thorny questions. What else might Google be monitoring, now that it considers everything to be part of an IoT Home, and are there vulnerabilities in the casting protocol that hackers could exploit?
